Application security has become essential in today’s digital landscape. Hackers often target web apps, APIs, and cloud platforms to access sensitive information. A security breach can not only compromise data but also interrupt business operations and harm your brand’s reputation. Without robust application security measures, companies risk expensive penalties, downtime, and loss of customer confidence.
In this guide, you’ll discover what application security entails and why it matters. We’ll also cover contemporary protection techniques, including SAST, DAST, and IAST. Keep reading to learn more!
What is Application Security?

Here are some key strategies to strengthen application security throughout the software development lifecycle (SDLC):
- Incorporate security measures early: Establish security guidelines and use tools during the design and development stages. For instance, conduct vulnerability scans while writing code.
- Protect applications in live environments: Apply security protocols and monitoring systems to keep applications safe once they are in production, such as performing ongoing security tests.
- Enforce strong authentication: Require robust login and access controls for applications handling sensitive or critical information.
- Leverage protective systems: Utilize technologies like firewalls, web application firewalls (WAF), and intrusion prevention systems (IPS) to block potential threats.
Types of Application Security
Application security is not a single layer or tool. It consists of multiple components that work together to protect applications from different types of threats. These components can be viewed through two main perspectives: security features built into applications and security categories based on how and when protection is applied.
Application Security Features
Application security features refer to the built-in mechanisms that help prevent, detect, and respond to attacks. These features are often integrated directly into the application or its supporting infrastructure. Common examples include authentication and authorization controls, data encryption, secure session management, input validation, and detailed logging. When implemented correctly, these features form the first line of defense against common vulnerabilities and misuse.
Application Security Categories
Application security categories describe the methods and approaches used to test, monitor, and protect applications at different stages of their lifecycle. This includes techniques applied during development, such as static analysis, as well as methods used after deployment, such as dynamic testing and runtime protection. Together, these categories help organizations identify weaknesses early, monitor real-world behavior, and continuously improve their security posture as threats evolve.
Understanding the Value of Application Security
In today’s digital landscape, software applications are central to business operations, customer interactions, and data management. This makes them prime targets for cyber threats, including data breaches and ransomware attacks. Understanding the value of application security helps organizations realize why investing in it is essential for business resilience.
Protects Sensitive Data
Application security safeguards confidential information such as customer details, financial records, and intellectual property. A breach can lead to financial loss, legal penalties, and serious damage to reputation. Strong security measures reduce these risks by preventing unauthorized access and data leaks.
Ensures Operational Continuity
A compromised application can disrupt important business processes, causing downtime and productivity loss. Application security lowers the risk of such disruptions, helping businesses maintain smooth operations even when facing potential threats.
Builds Customer Trust
Users expect the software and services they use to be safe. Implementing robust application security shows a company’s commitment to protecting user data, which strengthens customer confidence and loyalty.
Reduces Long-Term Costs
While security measures require upfront investment, the cost of managing breaches, including recovery, legal fees, and reputational damage, is much higher. Proactively securing applications helps organizations save money and resources over time.
Supports Compliance Requirements
Many industries have regulatory standards that require organizations to implement application security. Meeting these standards helps avoid fines and ensures businesses operate responsibly.
Common Application Security Risks
Understanding potential security risks is crucial to building and maintaining secure applications. Below are some of the most frequent threats that organizations face, along with explanations of their impact.
Broken Access Control
When access controls are not correctly enforced, both malicious actors and regular users can gain permissions they shouldn’t have. Common scenarios include:
- Attackers accessing accounts without authorization, potentially performing actions reserved for administrators or other users.
- Users receive privileges that exceed their intended role, allowing them to carry out restricted operations.
To address these risks, implement robust access control policies that clearly define roles, enforce the principle of least privilege, and isolate sensitive functions according to user responsibilities.
Cryptographic Failures
Weaknesses in Encryption and Data Protection happen when sensitive information is not adequately secured both during storage and while being transmitted over networks. Inadequate protection can make critical data, including user passwords, financial details, medical records, and personal information, accessible to attackers.
The consequences of such vulnerabilities extend beyond technical risks. Organizations may face violations of privacy laws and industry standards, such as the European Union General Data Protection Regulation (GDPR) and Payment Card Industry Data Security Standard (PCI DSS). These violations can result in significant financial penalties, loss of customer trust, and long-term reputational damage.
Proper encryption practices, key management, and consistent application of security protocols are essential to prevent unauthorized access and ensure compliance with regulations.
Insecure Design
Insecure design occurs when security is not properly considered during the planning and architecture stages of an application. Instead of being caused by a single coding mistake, these weaknesses arise from missing or ineffective security controls built into the application from the start. As a result, the software may be fundamentally unprepared to handle serious threats.
What makes insecure design particularly risky is that it cannot be fully corrected through configuration changes or quick fixes after deployment. Even well-written code can remain vulnerable if the underlying design does not account for real-world attack scenarios. To avoid these issues, organizations must embed security thinking into the design process, ensuring that applications are structured to withstand threats long before they go live.
Security Misconfigurations
Security configuration gaps arise when systems and applications are not properly secured across their entire technology stack. These weaknesses often appear when environments are deployed with default or overly permissive settings, leaving applications unnecessarily exposed to attacks.
Common examples include:
- Granting excessive or poorly defined permissions to cloud services
- Keeping unused features, services, or components active
- Failing to change default credentials or administrative accounts
- Allowing unsafe XML processing that can lead to XML External Entity (XXE) attacks
Vulnerable and Outdated Components
This risk arises when applications rely on software libraries, frameworks, or dependencies that are no longer supported or contain known security flaws. These weaknesses often appear when development teams lack full visibility into the components and versions used within an application.
As a result, attackers can exploit publicly disclosed vulnerabilities to compromise systems. Keeping software components updated and maintaining a clear inventory of dependencies is essential to reducing this risk.
Identification and Authentication Failures
Identity and authentication weaknesses arise when applications fail to properly verify who a user is or manage user sessions securely. These issues, formerly known as broken authentication, can expose systems to account takeovers, unauthorized access, and identity-based attacks.
To reduce these risks, applications must implement reliable authentication mechanisms and consistently validate all user identities. Equally important is secure session management, which helps prevent attackers from hijacking active sessions and exploiting authentication gaps.
Software and Data Integrity Failures
Software and data integrity issues arise when applications lack reliable mechanisms to ensure that code and data remain unaltered by unauthorized actions. These risks often surface during software updates, data changes, or modifications within CI/CD pipelines that are not properly verified.
When delivery pipelines are insecure, attackers can exploit them to inject malicious code, gain unauthorized access, or carry out large-scale supply chain attacks. Protecting integrity across the development and deployment process is essential to maintaining trust in the application.
Security Logging and Monitoring Failures
Failures in security logging and monitoring occur when an application is unable to effectively identify, track, or respond to suspicious activity. These capabilities are vital for detecting breaches early and understanding how an attack unfolds.
Without adequate logging, monitoring, and alerting mechanisms, security teams lose visibility into system behavior, making incident response, investigation, and recovery significantly more difficult. Over time, this lack of insight increases both the impact and cost of security incidents.
What Is Application Security Testing?
Application Security Testing (AST) refers to the systematic process of identifying, analyzing, and mitigating security vulnerabilities within software applications. It evaluates application code, components, and runtime behavior to ensure that security weaknesses are detected and addressed before they can be exploited. In modern development environments, application security testing is essential for maintaining secure, reliable, and compliant applications.
Types of Application Security Testing
To effectively reduce application security risks, organizations rely on multiple testing approaches. Each method targets different stages of the application lifecycle and uncovers specific types of vulnerabilities.
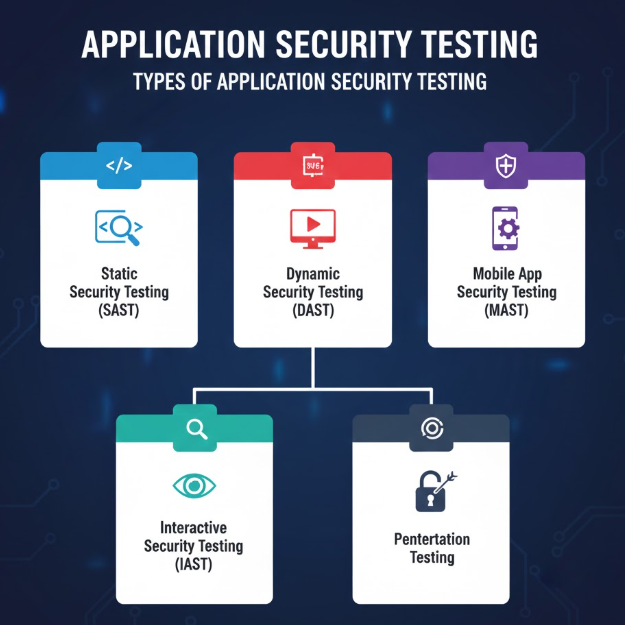
Static Application Security Testing (SAST)
SAST examines an application’s source code, bytecode, or binaries without executing the program. This method allows security teams and developers to detect vulnerabilities early, such as insecure coding patterns, logic flaws, or improper data handling.
This is because SAST operates during the development phase, it is well-suited for identifying issues before the application is deployed. It also supports secure coding practices by providing developers with actionable feedback while writing code.
Dynamic Application Security Testing (DAST)
DAST analyzes running applications by simulating real-world attacks from an external perspective. Instead of reviewing code, it focuses on how the application behaves in production or staging environments.
This approach is effective for uncovering vulnerabilities like injection attacks, authentication weaknesses, and configuration issues that only appear during runtime. DAST helps organizations understand how attackers might exploit an application once it is live.
Interactive Application Security Testing (IAST)
IAST combines elements of both static and dynamic testing by monitoring applications during execution while analyzing the underlying code. It provides more precise vulnerability detection with fewer false positives.
As a result IAST operates in real time, it enables faster remediation by linking runtime behavior directly to specific lines of code. This makes it particularly valuable in agile and DevOps environments.
Mobile Application Security Testing (MAST)
Mobile Application Security Testing, commonly known as MAST, focuses on identifying security risks unique to mobile apps. These tools evaluate mobile applications by analyzing both the application code and its behavior during runtime, while also examining diagnostic and usage data generated on mobile devices.
Businesses rely on MAST solutions to uncover vulnerabilities and mobile-specific threats, including compromised devices, unintended data exposure, and unsafe network connections such as malicious or unsecured WiFi. By addressing these risks early, organizations can deliver more secure and reliable mobile experiences to users.
Penetration Testing
Penetration testing simulates real cyberattacks to assess how secure an application truly is. It applies attacker-style techniques such as injection attacks, cross-site scripting, and privilege abuse to uncover weaknesses in both technical defenses and application logic.
This approach can also be used to evaluate API security and may be conducted manually, automatically, or in combination. For organizations handling sensitive data, penetration testing plays a critical role in meeting compliance requirements and reducing security risks.
Application Security Tools and Solutions
Modern applications demand more than basic security measures. With the right tools and solutions, businesses can proactively manage risks and strengthen their defenses.
Application Discovery
Application discovery focuses on identifying all applications, services, and APIs within an organization’s environment. In many cases, security risks emerge not from known systems, but from overlooked or undocumented applications, including legacy systems and shadow IT.
By establishing a complete and accurate inventory, organizations gain visibility into their true attack surface. This visibility is critical for applying consistent security controls and avoiding gaps that attackers can exploit.
Application Assessment
Application assessment evaluates the security posture of an application by examining its architecture, configuration, logic, and potential attack paths. Rather than simply listing vulnerabilities, assessments help identify how weaknesses could be exploited in real scenarios.
This deeper understanding allows organizations to prioritize remediation efforts based on risk severity and exposure, rather than addressing issues in isolation.
Software Composition Analysis (SCA)
Most modern applications are built using open-source libraries and third-party frameworks. Software Composition Analysis identifies these components and scans them for known vulnerabilities, outdated versions, and licensing issues.
Without SCA, organizations may unknowingly deploy applications with publicly disclosed vulnerabilities that attackers actively target.
Software Bill of Materials (SBOM)
An SBOM provides a structured inventory of all components used within an application. It improves transparency and traceability by documenting exactly what software dependencies exist and where they are used.
SBOMs enable faster response when new vulnerabilities are discovered and support compliance requirements that increasingly demand visibility into software supply chains.
Vulnerability Management
Vulnerability management is a continuous process that tracks security issues from discovery through remediation. It consolidates findings from multiple tools and helps teams prioritize fixes based on real-world risk.
By maintaining an ongoing view of application vulnerabilities, organizations can reduce exposure over time instead of reacting only after incidents occur.
Web Application Firewall (WAF)
A web application firewall monitors and filters incoming traffic to block common attack patterns such as injection attacks, cross-site scripting, and automated bot activity.
WAFs are particularly effective for protecting internet-facing applications and APIs, serving as a defensive layer that reduces immediate exposure to known threats.
Runtime Application Self-Protection (RASP)
RASP operates from within the application at runtime, allowing it to observe application behavior and detect attacks as they occur. When malicious activity is identified, RASP can intervene immediately.
This internal visibility makes RASP effective even against attacks that bypass perimeter defenses or exploit previously unknown vulnerabilities.
Cloud-Native Application Protection Platforms (CNAPP)
CNAPP solutions are designed to secure applications built and deployed in cloud environments. They provide unified visibility across workloads, identities, configurations, and application behavior.
By consolidating multiple security functions into a single platform, CNAPP helps manage the complexity of cloud-native application security.
Application Monitoring
Application monitoring provides continuous insight into application performance, behavior, and security events. It enables early detection of anomalies that may indicate attacks, misuse, or system instability.
Ongoing monitoring supports faster incident response and helps maintain application reliability in production environments.
Intrusion Prevention Systems (IPS)
Intrusion Prevention Systems (IPS) monitor network traffic in real time to detect and block malicious activity before it reaches applications. By analyzing traffic patterns and known attack signatures, IPS can automatically stop threats such as exploitation attempts, brute-force attacks, and malicious scans.
IPS works at the network layer and acts as a preventive barrier, reducing the number of attack attempts that reach the application. While it cannot understand application logic, it plays a critical role in limiting exposure and strengthening defense in depth.
Application Migration Security
Application migration security protects applications during transitions between environments, such as moving from on-premises systems to the cloud. Migrations often introduce new risks due to configuration changes, expanded access permissions, or newly exposed services.
This security approach ensures that access controls, data protection, and monitoring remain effective throughout the migration process. It helps prevent security gaps from appearing during and after the transition to a new environment.
Application Security Best Practices
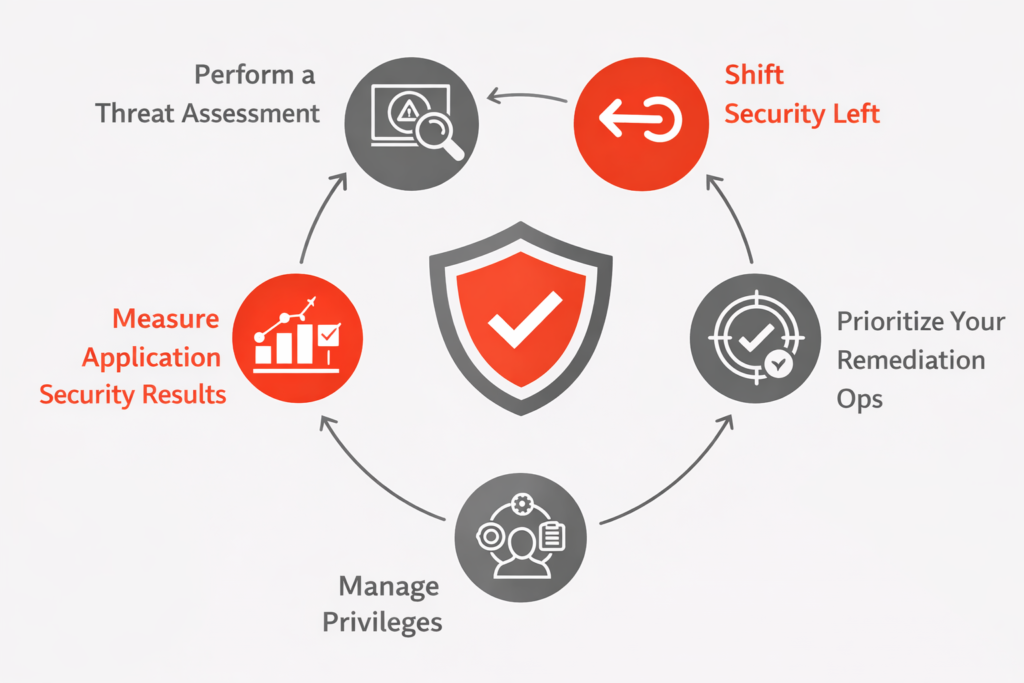
Below are key practices that can significantly improve how you implement and manage application security.
Threat Assessment
Start by identifying the most sensitive assets within your application. This helps you understand potential attack paths, evaluate current security controls, and decide whether additional protections are needed.
At the same time, set realistic security expectations. No application is completely immune to attacks, and security efforts must be sustainable over the long term. Overloading teams with excessive requirements can weaken compliance and consistency. Effective application security is an ongoing effort that relies on both technology and collaboration across the organization.
Shift-left security
Shift-left security refers to the practice of introducing application security at the earliest stages of the secure software development lifecycle (SDLC). Instead of postponing security checks until the end of development, organizations embed security testing directly into the CI/CD pipeline.
This forward-looking DevSecOps strategy delivers several advantages. It encourages closer collaboration between development and security teams, allowing releases to move faster without compromising safety. By detecting and resolving vulnerabilities early, teams can improve overall code quality and avoid costly rework later. In addition, shift-left security supports regulatory compliance while minimizing delays in the delivery process.
Manage Privileges
Effective application security starts with strict control over who can access what. Systems that support core business functions or store sensitive information should never allow broad or permanent access. Instead, permissions should be granted selectively, based on real operational needs and removed when they are no longer required.
This access model is commonly described as least privilege, and it plays a vital role in reducing security risks:
- When attackers breach low-level user accounts, limited permissions prevent them from moving deeper into critical systems or accessing valuable data.
- Security threats do not always come from outside the organization. Excessive internal access can magnify the impact of human error or malicious behavior, making it essential to keep permissions tightly scoped at all times.
Prioritize Your Remediation Ops
As the number of software vulnerabilities continues to rise, development teams are often overwhelmed by the sheer volume of issues that require fixes. Trying to address everything at once is unrealistic, which makes smart prioritization essential for maintaining application security.
To prioritize effectively, organizations must evaluate threats based on multiple factors. This includes vulnerability severity scores such as CVSS, as well as the business and operational criticality of the impacted application. For open-source risks in particular, it is important to determine whether your proprietary code actually relies on the vulnerable functionality. If the affected feature is not used or triggered within your product, the vulnerability may carry a high severity score but pose little to no real-world risk.
Measure Application Security Results
Tracking and communicating the performance of your application security initiatives is essential. Start by selecting the indicators that matter most to stakeholders and leadership. These metrics should be presented in a clear, practical format that supports decision-making and helps secure long-term commitment to the program.
At the early stages, flooding executives with excessive data can create confusion rather than clarity. Instead, focus on demonstrating how the application security strategy aligns with internal security standards, while clearly highlighting measurable improvements such as fewer vulnerabilities, lower risk exposure, and stronger application stability.
Final Thoughts
Application security has become a critical requirement for modern businesses, not just a technical concern. As cyber threats continue to evolve, organizations need a structured and proactive approach to securing their applications across the entire lifecycle.
Sphinx delivers practical application security solutions designed to help businesses identify vulnerabilities, reduce risk, and maintain operational stability. By combining security best practices with real-world implementation experience, Sphinx supports organizations in building and running applications that are secure, resilient, and ready to scale.




CEO - Son Le
OTHER BLOGS
Blogs
Top 15 HRM Software for Effective HR Management 2026
In 2026, Human Resource Management expands beyond payroll processing and employee record keeping to play a strategic role in business growth. Modern HR teams are expected to drive talent strategy, enhance employee experience, ensure regulatory compliance, and deliver workforce insights that directly support business growth. As organizations become more digital...
Read MoreBlogs
AI Automation: How It Works, Benefits, and Best Practices
As organizations face increasing operational complexity, traditional automation alone is no longer sufficient to sustain efficiency and competitiveness. Businesses today require systems that not only execute predefined tasks but also learn, adapt, and make intelligent decisions. This shift has positioned AI Automation as a transformative force, enabling enterprises to automate...
Read MoreBlogs
App Design for 2026: Trends, Techniques, and Tools
As digital products become more deeply embedded in everyday life and enterprise operations, app design in 2026 is no longer about visual appeal alone. It is a strategic discipline that combines user psychology, business objectives, platform capabilities, and emerging technologies. Modern app design must anticipate user intent, adapt to contextual...
Read MoreOTHER BLOGS
Our Sevices
IoT Development
SphinX offers cutting-edge IoT development services, seamlessly connecting devices and providing innovative solutions for a...
Xem thêmOur Sevices
Blockchain Development
We are highly proficient in engineering reliable and secure blockchain technologies from the ground up,...
Xem thêmOur Sevices
ERP & CRM Development
ERP & CRM development services that you need! Streamline business processes and enhance organizational efficiency....
Xem thêmOTHER BLOGS
Our Sevices
IoT Development
SphinX offers cutting-edge IoT development services, seamlessly connecting devices and providing innovative solutions for a...
Xem thêmOur Sevices
Blockchain Development
We are highly proficient in engineering reliable and secure blockchain technologies from the ground up,...
Xem thêmOur Sevices
ERP & CRM Development
ERP & CRM development services that you need! Streamline business processes and enhance organizational efficiency....
Xem thêm